If you handle customer data, you’re probably already familiar with SOC 2 audits. And if you’re planning to use Amazon Web Services (AWS) to store, process, or transmit customer data, you need to know how to prepare for a SOC 2 audit on AWS. In this blog post, we’ll give you an overview of SOC 2 and what it covers, explain the key difference between SOC 1 and SOC 2 audits, and provide some tips on how to prepare for AWS SOC compliance.
In this Guide:
- What is a SOC2 Audit?
- How Do I Become SOC 2 Compliant in AWS?
- What Information Do the AWS SOC Reports Provide?
- Which Services are in Scope for the AWS SOC 2 Reports?
- AWS Shared Responsibility Model
- AWS Services and Tools to Support SOC 2 Compliance
- Preparing for a SOC 2 Audit on AWS
- Engaging a Qualified CPA

What is a SOC2 Audit?
The SOC2 audit, a comprehensive evaluation process, probes an organization’s ability to safeguard its data responsibly, thereby ensuring the welfare of the organization and its stakeholders’ privacy. Created by the American Institute of CPAs (AICPA), it is a well-respected and globally recognized security standard validates service organizations’ control environment on their journey toward bolstering security, availability, confidentiality, and privacy.
Diving deeper into the audit process, the SOC2 audit scrutinizes companies using five trust service principles. These principles, namely security, availability, processing integrity, confidentiality, and privacy, are the pillars for system and organization controls. These control elements act as the safety net for your data, preserving its integrity and protecting it against potential cyber threats.
What sets the SOC2 audit apart from other audits is its two-tier system of examination: Type1 and Type2. The Type1 assessment acts as a snapshot of your organization’s controls at a particular point in time. Conversely, Type 2 extends this examination over time, comprehensively analyzing your control environment’s functioning.
The Interplay between SOC2 Audit and AWS
AWS, as a leading cloud service provider, maintains an extensive set of security availability and confidentiality controls that align perfectly with the trust service principles advocated by SOC2. These controls, often termed AWS-defined controls, ensure an impenetrable shield for the AWS customers’ data while promoting accessibility and reliability.
When subjected to a SOC2 audit, AWS’s control environment is thoroughly scrutinized for its compliance with the trust service principles. The audit report generated at the end of the process provides an accurate depiction of AWS’s adherence to the standards set by the AICPA.
This external audit also includes an analysis of the AWS customers’ data handling procedures, including data encryption, backup, restoration, and access control measures. This allows the auditors to perform analytics on AWS’s procedures and ascertain the level of security provided.
Furthermore, the SOC2 audit also reviews certain site features in AWS, such as firewall and network security, intrusion detection, and disaster recovery plans. These features form part of the wider scope of system and organization controls, including the technological measures in place and the personnel, procedures, and policies that are crucial for maintaining data integrity.
Understanding the Key Differences between SOC 1, SOC 2, and SOC 3
How Do I Become SOC 2 Compliant in AWS?
One of the benefits of using a mature platform like AWS is that they have a built-in system for helping organizations meet SOC2 compliance. Firstly, AWS provides organizations with several inherited controls related to SOC2, which means that most organizations will not have to implement any additional security controls to meet SOC2 compliance. Secondly, AWS provides SOC reports related to SOC1,2 & 3 that outline how AWS services meet SOC2 compliance. These reports describe the AWS Controls environment and external audit of AWS controls that meet the abovementioned AICPA Trust services.
What Information Do the AWS SOC Reports Provide?
Leveraging the advanced capabilities of a mature platform such as AWS can simplify the journey toward SOC 2 compliance for your organization. AWS provides a structured and efficient pathway to achieve SOC 2 compliance, empowering your organization with robust controls and audit reports.Utilizing AWS Inherited Controls
AWS offers a host of inherited controls related to SOC 2, which forms a pivotal part of the AWS control environment. These controls cater to the security, availability, and confidentiality needs of AWS users. Negating organizations’ need to establish additional security controls to meet SOC 2 compliance.
Inherited controls refer to the protections and mechanisms that AWS already has in place. These span across multiple domains such as physical security of data centers, network security, access controls, and data encryption, among others. The advantage of these inherited controls is that they reduce the overall effort and resources organizations require to meet compliance.
Understanding AWS SOC Reports
AWS offers comprehensive SOC reports related to SOC 1, 2, and 3. These reports detail how AWS services conform to SOC 2 compliance, providing a transparent view of the AWS control environment. They delineate the AWS controls that satisfy the AICPA Trust services and the results of the external audit of AWS controls.
The information available in these reports can guide your organization’s efforts toward SOC 2 compliance. They also serve to assure your organization of AWS’s robustness and commitment to maintaining a high-security environment.
Utilizing Relevant Tools and Technologies
AWS CloudTrail, for instance, provides event history of your AWS account activity for governance, compliance, operational auditing, and risk auditing. Similarly, AWS Config is a service that enables you to assess, audit, and evaluate the configurations of your AWS resources. These services, among others, can simplify compliance efforts by providing relevant content and useful site features.
Collaborating with Third Parties
To supplement AWS’s capabilities, approved third parties like Oppos Cybersecurity Experts can provide additional insights into your organization’s compliance status. These experts can review your control environment, suggest improvements, and offer guidance on the effective use of AWS’s offerings. Furthermore, they can provide anonymous statistics for benchmarking and advertising category allowed blocking relevant advertising, thereby helping you to enhance your control environment.
Which Services are in Scope for the AWS SOC 2 Reports
These services go through a rigorous process to ensure they meet the required security, availability, and confidentiality report criteria.
SOC reports covering an extensive list of AWS services, with the scope reviewed regularly to cater to evolving customer needs. The latest SOC reports reflect this scope.
Some key AWS services within the scope of SOC reports include, but are not limited to:
- Data Storage and Database Services: Amazon DocumentDB, Amazon DynamoDB, Amazon Elastic Block Store (EBS), Amazon Simple Storage Service (S3), Amazon Redshift, and Amazon Relational Database Service (RDS) among others.
- Compute Services: Amazon Elastic Compute Cloud (EC2), Amazon EC2 Auto Scaling, and Amazon Elastic Kubernetes Service (EKS), to name a few.
- Networking Services: Amazon Virtual Private Cloud (VPC), Amazon Route 53, and Amazon API Gateway.
- Management & Governance Services: AWS CloudTrail, AWS Config, AWS Control Tower, and AWS Organizations.
- Security, Identity & Compliance Services: AWS Identity and Access Management (IAM), AWS Key Management Service (KMS), Amazon Macie, and AWS Security Hub.
AWS encourages organizations to liaise with their AWS account team to discuss workload objectives and goals. This conversation can provide insights into the proposed use case, the architecture, and how AWS’s security and compliance processes overlay that architecture.
If an AWS service is not listed as being in the scope of the most recent assessment, it does not imply that it cannot be used. The nature of the data being processed or stored in the service will determine if it impacts the compliance of the customer data environment.
For a detailed and updated list of AWS Services in Scope of SOC reports, organizations can refer to AWS’s official documentation and connect with an AWS business representative.
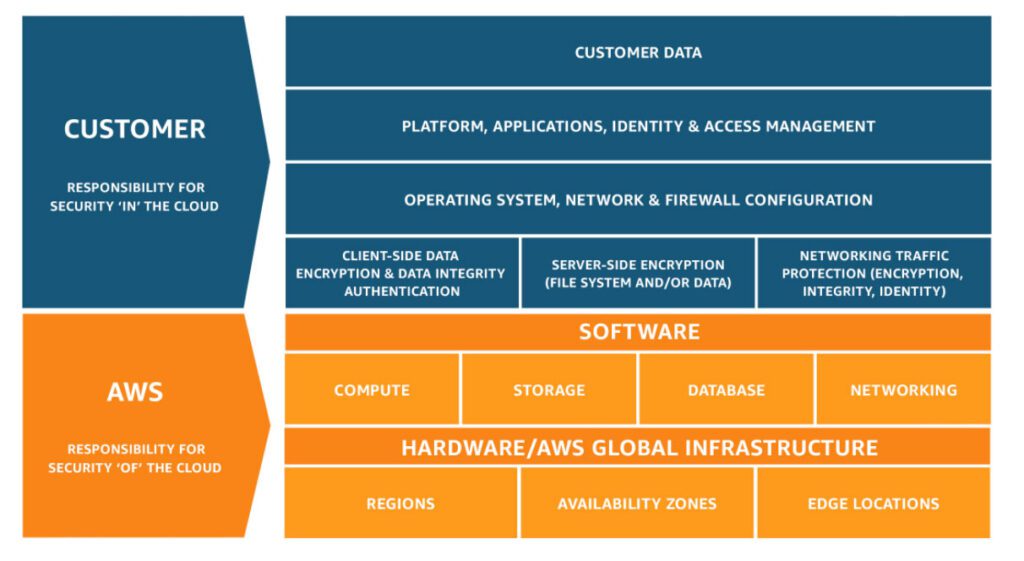
AWS Shared Responsibility Model
The shared responsibility model is the idea that security and compliance are shared responsibilities between AWS and their customers. Under this model AWS will operate, manage and control the components from the host operating system and virtualization layer down to the physical security of the systems. The customers’ responsibility will include managing the guest operating system and configuring the AWS-provided security controls. From a SOC2 perspective, this means that even though AWS will provide you with SOC2 reports there is still work that needs to be done by the organization to ensure you meet compliance.
AWS Services and Tools to Support SOC 2 Compliance
There are some AWS tools that you can use to in your cloud environment to improve your security and meet cloud compliance significantly:
- AWS Config: This is Amazon’s configuration monitoring tool. You can use AWS Config to assess how well your resource configuration aligns with your internal standards, industry guidelines or specified regulations. It’s a great tool for ensuring your internal resources meet your desired standards.
- AWS Artifact: This tool provides security and compliance reports based on auditors testing over 2,600 standards and requirements in the AWS environment in a given year. AWS Artifact provides on-demand access to reports proving your compliance with SOC2.
- CloudTrail: This is Amazon’s logging and monitoring solution. Cloudtrail allows you to track and automatically respond to malicious activity in your company’s environment.
- SNS: This is Amazon’s notification service. It can be integrated with other Amazon web services to ensure that users are notified in the event of specific events.
These are some of the tools you can use to ensure that your organization meets SOC2 requirements in your AWS environment.
Preparing for a SOC 2 Audit on AWS
Amazon a tool known as AWS Audit Manager, this tool allows you to assess your internal security posture using prebuilt frameworks. Audit manager has a prebuilt framework for SOC2 compliance that guides you on the exact controls you need in place in AWS to achieve SOC2 compliance. It also collects evidence from those tools that can be used later to prove that the controls are not only in place but working as intended. For full details on the SOC2 framework, you can read the aws documentation here.
Engaging a Qualified CPA
Once you have everything in place that you need to meet compliance, the final step is to find a qualified CPA or CPA firm to perform the final audit. SOC2 examinations can only be performed by CPAs, and this will be required to get certified.
Conclusion
AWS offers many services and software tools that assess companies with improving their security and meeting SOC2 compliance. However, identifying and implementing all of these security solutions can be a daunting task for people that don’t have the proper experience. Getoppos security consultants have several years of experience helping clients with AWS environments prepare for and pass SOC2 compliance audits.
If you’re a company looking to meet SOC2 compliance contact us for a free cybersecurity consultation. Oppos Cybersecurity Consultants in Canada provides robust solutions to guide your organization toward SOC2 compliance. Our team of cybersecurity experts understands the complexities and nuances of securing data in the cloud. Whether your organization is small or mid-sized, we will help you navigate the complexities of using AWS services to meet SOC2 compliance standards.
Don't wait – secure your data with Oppos' SOC 2 Compliance
AWS SOC 2 FAQS
AWS Audit Manager and artifact support SOC1,2 & 3 compliance.
AWS SOC reports are released two per year, roughly in May and November.
You can get SOC1 or SOC2 reports on demand from AWS artifact.




