Oppos’ Penetration Testing services are designed to help businesses and organizations enhance their cybersecurity posture. Our team of experts simulates a real-world attack on your key systems and infrastructure, going beyond traditional vulnerability scans to identify blind spots and provide actionable insights. Our penetration testing services are designed to validate your cyber defences against real-world threats and provide meaningful, actionable insights to help improve your system’s vulnerabilities.
At Oppos, we understand that finding your weaknesses can be the hardest part of enhancing your cybersecurity. That’s why we bring together front-line threat intelligence, years of experience conducting cyber security assessments, and a team of certified experts to deliver sophisticated and scalable penetration testing services. We don’t just highlight your vulnerabilities. We provide the knowledge and expertise to help you strengthen your defences and better prepare for potential attacks.
With Oppos cybersecurity experts, you can rest assured that your cyber defences are being tested by a team of experts who have completed hundreds of assessments. Trust us to provide the foundation for your business’s stronger, more secure future.

What is Penetration Testing?
Penetration testing, also known as “pen testing,” is an essential cybersecurity assessment. It helps organizations identify and mitigate vulnerabilities in their systems, networks, devices, and applications. By conducting penetration tests, businesses can gain valuable insights into their security controls, understand potential risks, and prioritize areas for improvement to protect sensitive data.
Penetration tests are performed by skilled security professionals, often called “ethical hackers”. Penetration testers used the same tools and techniques as malicious attackers to gain access to the target system. They simulate real-world attacks to uncover security weaknesses and evaluate the effectiveness of existing security measures. The goal is to identify vulnerabilities before malicious actors do, enabling organizations to strengthen their security infrastructure and minimize the risk of a successful cyberattack.
Penetration testers use various testing tools, including cloud pen testing tools, to evaluate various security controls. The process often starts by gathering information about the target system. This includes IP addresses, domain names, and others that may help identify security vulnerabilities. These vulnerabilities are explored to gain access, maintain access, and potentially exfiltrate sensitive data from the computer system.
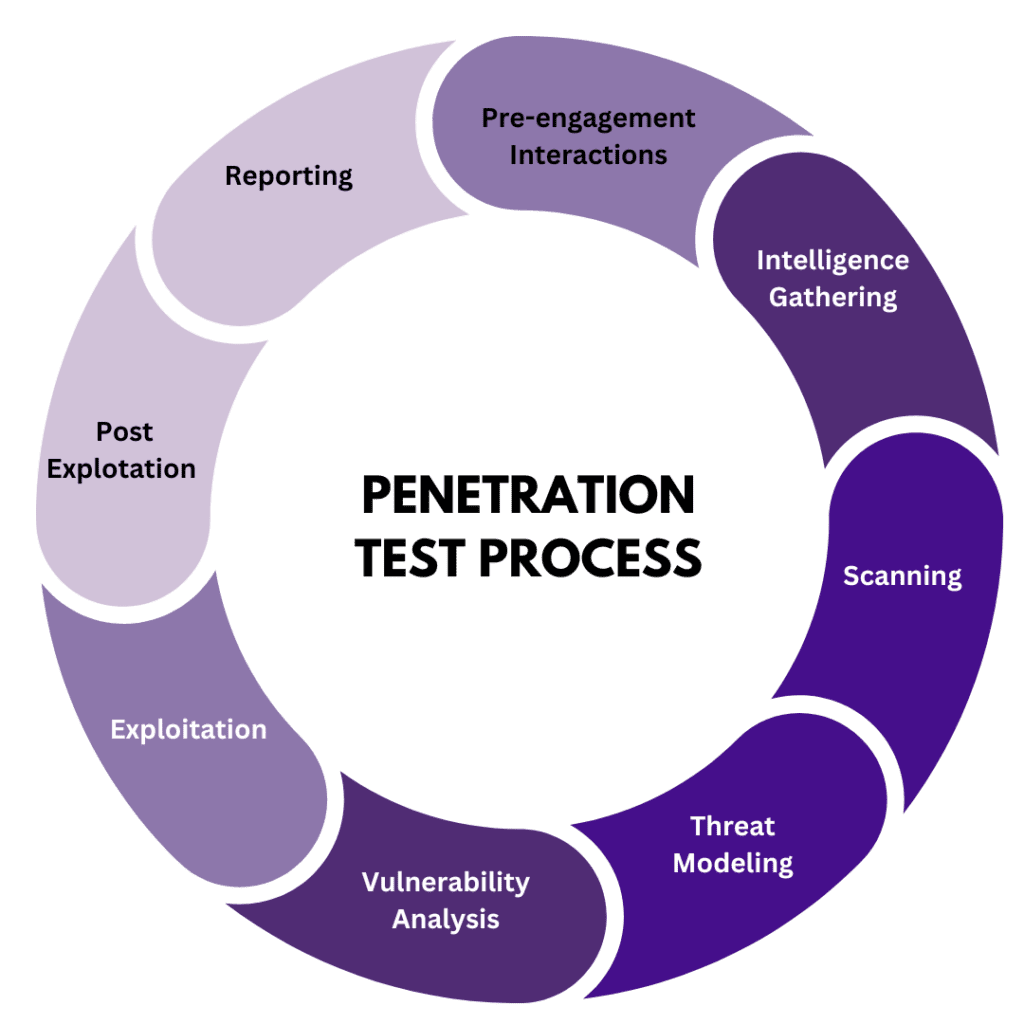
Different types of penetration tests are performed according to the organization’s needs and goals. Cloud technologies, for example, require specialized cloud pen testing to assess the security of cloud-based infrastructure and applications.
Pen test is crucial in today’s increasingly threat-filled environment. Many standards and regulations, such as PCI-DSS and ISO27001, mandate yearly pen testing to demonstrate compliance with laws and regulations. By uncovering and prioritizing vulnerabilities, pen tests help organizations improve their security posture and reduce the risk of a successful cyberattack.
The importance of pen tests cannot be overstated for organizations that process or store customer information. These assessments provide invaluable insights into the strengths and weaknesses of their systems. This enables them to make data-driven decisions about where to invest in security enhancements.
During a simulated, authorized cyberattack, penetration testers uncover vulnerabilities and prioritize areas for improvement, ensuring that the organization’s security measures are up-to-date and effective against real-world threats.
Why Do You Need Penetration Testing?
In today’s digital landscape, pen testing is essential for businesses of all sizes to safeguard their systems and data. By employing pen testing tools, ethical hackers can simulate attacks on your network, identifying security gaps and weaknesses in your security controls.
Pen testing is vital for startups, midsize companies, and large enterprises, as it helps maintain access and prevents potential financial and reputational damage from breaches.
Trust our experienced cyber security personnel to fortify your core security with comprehensive pen tests, ensuring your organization’s highest level of protection.
Startups engaging with other businesses must prioritize pen testing, as clients often request pen test results to gauge the security level of provided services. Our expert pen testers use cutting-edge pen testing tools to simulate attacks on your IT infrastructure, identifying system vulnerabilities and security gaps in your network devices.
By conducting a thorough vulnerability assessment, using both public and private sources, we help startups bolster their IT environment and internal structure. Gaining assurance in your system’s security is crucial for maintaining access and fostering trust with your clients. Let our ethical hackers fortify your core security today.
As midsize companies experience continuous growth and change, pen testing becomes indispensable to maintaining a secure IT system. Our skilled penetration testers conduct comprehensive security assessments, including simulated attacks on web applications, to ensure that your evolving environment remains protected.
Our team effectively guards against cybercriminals and threat actors seeking unauthorized access by utilizing ethical hacking techniques and identifying potential threats.
With our pen testing services, you can trust that your midsize company’s IT security remains robust even as your business expands and adapts to new challenges.
For large enterprises, implementing penetration testing programs is crucial in preventing financial and reputational damage caused by data breaches.
Our expert pen testers utilize ethical hacking techniques to conduct comprehensive security assessments, simulating attacks on web applications to identify potential vulnerabilities in your system. By proactively addressing these issues, we effectively mitigate the risk of devastating cyberattacks from threat actors.
Trust our pen testing services to secure your enterprise’s digital infrastructure and maintain your company’s strong reputation in an increasingly complex cybersecurity landscape.
In all cases, pen testing helps companies find security weaknesses before they are exploited by attackers. Such attacks could result in the theft of sensitive information, unauthorized use of server resources, or compromise of the company’s internal infrastructure through the vulnerable application.
Oppos Pen Testers: Way More Than Security Experts
At Oppos, we understand that the most effective defence against cyber threats is to adopt the mindset of an attacker. Our pen testers, with extensive knowledge of hacking tactics, excel in assessing a wide array of digital and physical attack surfaces and vectors. They are far more than just security experts; they are seasoned, ethical hackers dedicated to staying ahead of emerging threats.
Our pen testers invest their time in research, publishing articles, presenting at conferences, and developing cutting-edge open-source testing tools. This continuous pursuit of knowledge ensures that our team is equipped with the latest techniques and strategies to protect your company’s reputation and assets.
By choosing Oppos for your pen testing needs, you can benefit from the experience and expertise of a team that goes above and beyond in the field of cybersecurity. Our unique approach combines ethical hacking and social engineering tactics. Thus, ensuring that your organization remains secure and resilient in an ever-evolving digital landscape.
Network Penetration Testing Services
Oppos network penetration testing services are aimed at uncovering even the most elusive security risks and entry points that could be exploited by hackers to compromise your network infrastructure. We offer a range of specialized penetration testing services, including:
- External Network Penetration Testing
- Internal Network Penetration Testing
- Wireless Penetration Testing
- Mainframe Penetration Testing
- Industrial/SCADA Penetration Testing
By choosing Oppos as your cybersecurity partner, we will provide you with a comprehensive understanding of your network’s security posture. Take the necessary steps to strengthen it and protect your business from potential attacks! Contact Oppos today!
Application Penetration Testing Services
Our approach to penetration testing combines manual testing and automated tools to uncover even the most intricate business logic vulnerabilities. Our methodology is based on the OWASP Top 10 framework.
We offer a range of specialized application penetration testing services, including:
- Web Application Penetration Testing
- Mobile Application Penetration Testing (for iOS and Android)
- Web Services/API Security Testing
- Thick Client Penetration Testing
- Application Security Code Review
At Oppos, our objective is to equip you with a thorough understanding of the security posture of your application, enabling you to take the appropriate measures to fortify it and safeguard your business against potential cyber threats.
Cloud Penetration Testing Services
Our cloud penetration testing services are here to help secure all of your cloud-hosted assets, no matter the cloud provider.
- Amazon Web Services (AWS) Penetration Testing
- Microsoft Azure Penetration Testing
- Google Cloud Platform (GCP) Penetration Testing
- Microsoft Office 365 Security Audit
Don’t let unknown security risks jeopardize your cloud-based assets. Trust Oppos to provide you with the peace of mind that comes from knowing your cloud environment is secure.
Adversary Simulation Services
Our team of experts will simulate specific hacking scenarios to test the efficiency and resilience of your IT systems and employees in responding to a targeted cyberattack.
Our adversary simulation services include:
- Red Team Assessment
- Purple Team Assessment
- Phishing Test & Cybersecurity Awareness Campaign
What Type of Penetration Test is Right for You?
Black Box Testing
This type of pen testing mimics an external attacker trying to gain unauthorized access to the system. It assesses the overall security posture of the company and includes attempts to interfere with web application users or negatively impact the system.
Gray Box Testing
Gray box testing combines both black and white box techniques and focuses on the vulnerability of insider threats. It simulates an attacker who has some knowledge of the company’s internal workings and is more budget-efficient and time-saving than black box testing.
White Box Testing
The objective of white box testing is to uncover hidden vulnerabilities and improve detection rates. This pen testing allows the tester to delve deeper into the target environment and application source code to find vulnerabilities.
Does My Organization Need Pen Testing?
Here are five reasons why you need a penetration test:
- Detect Vulnerabilities Before Criminals Do: A penetration test can reveal vulnerabilities that a cybersecurity strategy may not have considered and help you patch any weak spots before a criminal finds them. It can also reveal vulnerabilities that cannot be detected with automated network vulnerability scanning.
- Test the Abilities of Your Network Defenders: A penetration test can analyze the ability of your IT professionals and intrusion detection programs to spot and respond to an attack. Pen tests also help identify areas where you need to improve your network defences.
- Assess the Potential Damage of a Successful Attack: A successful cyberattack can severely impact your business, including disruption of critical processes, damage to brand reputation, loss of key business data, and more. A penetration test can help you assess and plan for these impacts during the disaster recovery phase.
- Prove Security Effectiveness to Customers and Executives: With data breaches becoming common news, customers are increasingly concerned about their data safety. A penetration test can help prove to them that your company is airtight and to executives that investing in cybersecurity is necessary for defending critical company assets.
- Reduce Remediation Costs and Network Downtime: Scrambling to fix security holes following a breach can be expensive and cause a significant outage for your business operations and customers. By addressing the vulnerabilities a penetration test discovers, fixes are faster and less disruptive to your company.
“A large Telco client of ours required Moveable Online undergo a PCI-DSS gap assessment. After asking around within our circle or business associates, we were introduced to Oppos. They were able to aid us with the gap assessment, make recommendations to secure our environment and help prepare the documentation our client required. The process was quick, informative and we will engage Oppos for future compliance related activities, primarily our efforts with achieving PCI-DSS compliance.”
“They weaved in a layer of security that we had only dreamed of in the past – a next generation rewall — which they built, congured and deployed at the perimeter of our network. When called upon, even with the great distance between us, they provide onsite or remote support as required and always meet the mark. Since the time of our initial project, we have called upon Oppos several times for various IT and Security related projects which they have delivered on every time.”

Don't wait for a real attack to find out if your systems and employees are prepared.
Penetration Testing FAQS
The cost of a pen test can vary depending on the scope and complexity of the test. Generally, prices range from a few thousand to tens of thousands of dollars.
The amount of time required to perform a pen test depends on the scope of the test and the complexity of the systems being tested. It can take anywhere from a few days to several weeks.
A successful pen test can demonstrate compliance with certain security standards, but it is not a guarantee of compliance. It is important to consult with regulatory requirements to ensure that all necessary compliance requirements are met.
Yes, a pen test is necessary even if your company runs vulnerability scans. A penetration test can identify vulnerabilities that may not be detected by vulnerability scans.
Pen testing can be disruptive to the environment, but it should not cause any significant downtime. The pen testers should work closely with your IT team to minimize any disruptions and ensure that systems remain operational during the testing process.

