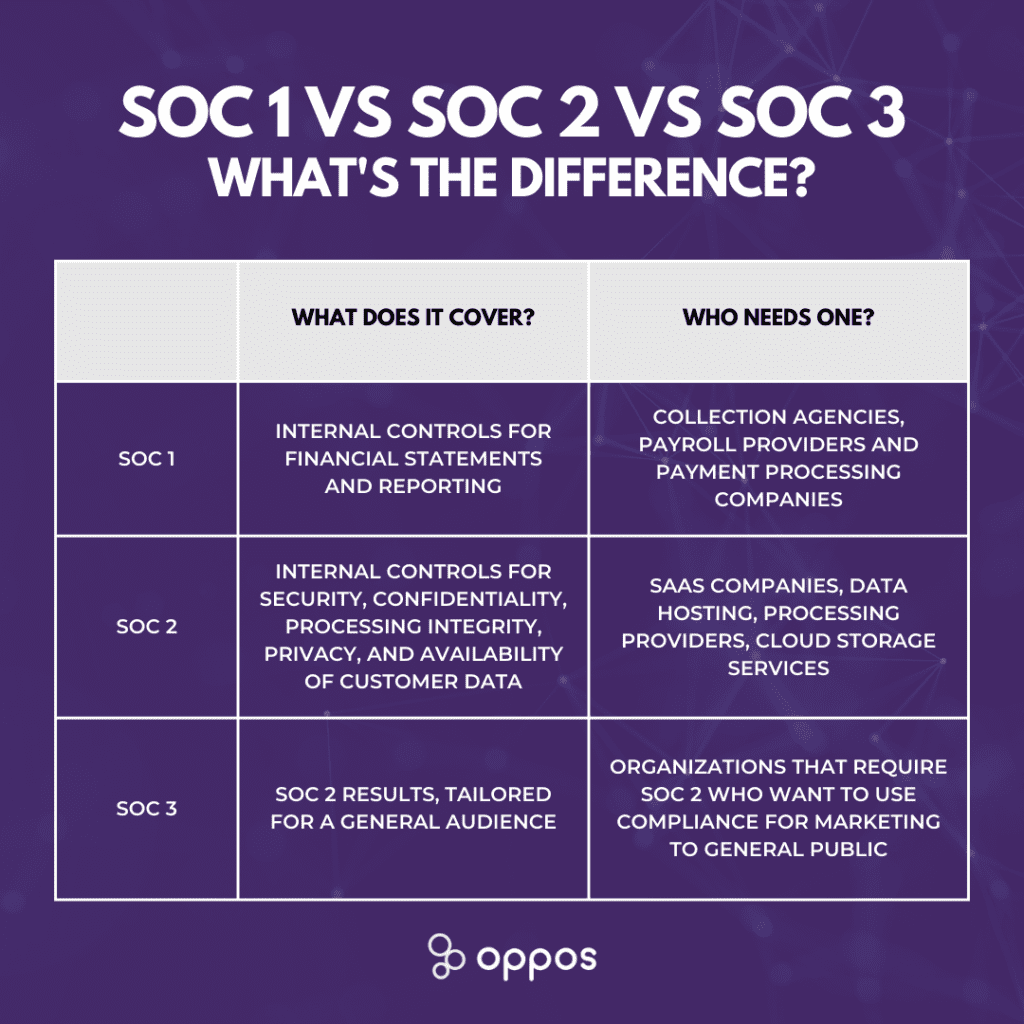
There are three types of SOC reports: SOC 1, SOC 2, and SOC 3. Organizations opt for SOC compliance when they want to reassure their customers that their data is safe. The three types of reports differ in terms of their content and audience. SOC 1 reports are financial audits that give your organization’s customers assurance that their financial information is being handled safely and securely.
SOC 2 focuses on assessing businesses in terms of their security controls. SOC2 is a compliance standard with an emphasis on security. SOC 3 focuses on assessing an organization’s security controls but it’s designed to be presented to a general audience rather than being used by stakeholders like SOC2. So, what’s the best SOC compliance framework for your business? Read on to learn more about the differences between the most common SOC reports.

What is SOC Compliance?
Protecting sensitive data has become a key concern as organizations rely more on technology-based service providers to manage critical aspects of their operations. To address this issue, service organizations have turned to SOC compliance. SOC or Service Organization Control is a set of standards created by the American Institute of Certified Public Accountants (AICPA) that outlines the necessary internal controls for safeguarding customer data. There are three tiers of SOC compliance: SOC 1, SOC 2, and SOC 3. Each tier has a specific focus, catering to different organizational needs. SOC 1 is centered around controls related to financial reporting, making it particularly relevant for accounting firms, data centers, and other entities involved in the processing of financial data. SOC 2, on the other hand, covers controls related to security, availability, confidentiality, and privacy, making it applicable for technology-based service organizations and information system services. Lastly, SOC 3 addresses controls related to security and confidentiality for public consumption, providing a more general overview of an organization’s controls. To achieve SOC compliance, organizations must first choose the appropriate tier and then implement the necessary controls to meet the requirements of that tier. This process may involve conducting attestation engagements to assess the organization’s controls and identify key control objectives. The result of these engagements is a SOC report, which documents the company’s internal financial controls and serves as proof of the organization’s commitment to its stakeholders. While achieving SOC compliance can be complex and costly, it is crucial for any organization that handles sensitive data, particularly small to medium-sized organizations seeking penetration testing services. By adhering to SOC compliance standards, these organizations can demonstrate their dedication to maintaining robust information technology processes and business processes, ensuring the security and integrity of their clients’ financial reporting.Why is SOC Certification Important?
SOC certification plays a pivotal role in demonstrating an organization’s commitment to robust security controls and procedures. As an independent confirmation, it provides assurance to customers and partners that a company takes the protection of their data seriously. In an increasingly competitive business environment, having SOC certification can be a deciding factor in winning new business, as many organizations now mandate that their vendors possess this certification.
One of the key benefits of SOC certification is that it allows organizations to assess their own security posture or evaluate the controls of potential vendors. By using SOC reports, companies can identify areas of improvement within their own internal controls, as well as gauge the risk of partnering with a particular service organization. This, in turn, helps mitigate risks in their own environment and ensures they make informed decisions when selecting vendors.
In essence, SOC certification is vital to a company’s cybersecurity strategy. It serves as a testament to the effectiveness of an organization’s controls. It provides valuable insights into the security of both their own operations and that of potential partners. By adhering to SOC compliance standards, small to medium-sized organizations looking for penetration testing services can demonstrate their dedication to upholding stringent information technology processes and business practices, ultimately instilling confidence in their stakeholders and partners.
When Does my Business Need an SOC Audit?
As your business grows, you may find that you need to take security more seriously. One way to do this is to get a SOC audit. SOC audits are designed to assess your business’s security posture and give you an idea of where you need to improve based on the AICPA standards. But when should you get one?
There are a few different factors to consider when deciding whether or not to get a SOC audit. First, think about the size and scope of your business. If you’re a large company with many employees and customers, you’ll need to take security more seriously than a small business. You have more data, more systems and the impact of a potential data breach is much larger so you should be taking your company’s security seriously.
Second, think about the sensitivity of your data. If you’re handling confidential information, you’ll need to be extra careful about security. Personally identifiable information (PII) can cause a lot of damage to individuals if it is stolen/leaked due to poor security practices. Additionally, this information is subject to laws and regulations that can lead to heavy fines, lawsuits and even revocation of business licenses if your organization is found to be negligent in your security practices.
Finally, think about your industry. Some industries are subject to more regulations than others, so you may need to get a SOC audit to comply with different industry regulations. You may also need SOC certification to win the trust of potential business partners or customers. SOC certification helps to prove to outside parties has good security practices and meet their security standards.
Types of SOC Reports
There are two types of SOC 1 reports: Type 1 and Type 2. A Type 1 report focuses on the design and effectiveness of controls at a specific point in time. A Type 2 report, on the other hand, focuses on the effectiveness of controls over a period of time. So which type of report is right for your organization? That depends on your needs and objectives. If you’re looking for a report that provides an overview of your controls and their effectiveness, a Type 1 report may be a good option. If you’re looking for a more in-depth report that covers the effectiveness of your controls over a period of time, a Type 2 report may be a better choice.SOC 1 VS SOC 2 vs Soc 3
SOC 1 Compliance
SOC 1 is a framework specifically designed to evaluate and document internal controls relevant to an audit of a user entity’s financial statements. As a part of the SOC compliance family, SOC 1 focuses on control objectives within a service organization’s process area, ensuring that these controls are effective and relevant.
A SOC 1 report is a comprehensive assessment of a service organization’s internal controls that directly impact a user entity’s financial reporting. The report is tailored to address the needs of user entities and their financial statement auditors. There are two distinct types of SOC 1 reports:
SOC 1 Type I Report: This report evaluates the service organization’s system, the suitability of the system controls for achieving control objectives, and the description on a specified date. SOC 1 Type 1 reports are generally restricted to user entities, auditors, and managers belonging to the service organization. A service auditor performs these reports in accordance with Statement on Standards for Attestation Engagements No. 16 (SSAE 16).
SOC 1 Type II Report: Building upon the analysis and opinions found in Type 1 reports, SOC 1 Type 2 reports also include views on the operating effectiveness of preestablished controls designed to achieve all related control objectives established in the description over a specified period. Control objectives in these reports address potential risks that internal controls aim to mitigate and encompass all relevant control domains.
SOC 1 compliance entails maintaining all SOC 1 controls documented within a SOC 1 report over a predefined period. In this context, compliance ensures the operating effectiveness of SOC 1 controls, which often include business process controls and IT general controls that provide reasonable assurance regarding control objectives. SOC 1 compliance may be required for publicly traded companies as part of their regulatory requirements.
The primary purpose of a SOC 1 report is to provide independent and actionable feedback on the effectiveness of a company’s internal safeguards and controls. As businesses increasingly demand these examinations, SOC 1 reports help financial statement auditors minimize audit processes and enable sophisticated service organizations to confirm the security and protection of their data and systems.
SOC 2 Compliance
SOC 2 compliance ensures the secure management of customer data. Based on AICPA’s Trust Services Criteria—security, availability, processing integrity, confidentiality, and privacy—SOC 2 compliance is tailored to the unique needs of each organization. By adhering to one or more trust services principles, organizations can design controls specific to their business practices. These internal SOC 2 reports provide valuable information to regulators, business partners, and suppliers about how an organization manages its data.
There are two types of SOC 2 reports:
- Type I Reports: Describes the organization’s systems and evaluates whether the system design complies with the relevant trust principles.
- Type II Reports: Details the operational efficiency of these systems.
Compliance with SOC 2 requirements signifies that an organization maintains a high level of information security. Rigorous compliance requirements, tested through on-site audits, help ensure sensitive information is managed responsibly. Some key benefits of SOC 2 compliance include improved information security practices and a competitive advantage, as customers prefer to work with service providers that demonstrate solid information security practices, particularly in IT and cloud services.
In addition to the basic security principle, organizations may need to comply with other SOC 2 principles, especially if they operate in industries where privacy and confidentiality are paramount, such as financial or banking sectors:
- Availability: Ensuring that customers can access the system according to the agreed terms of use and service levels.
- Processing Integrity: For financial or eCommerce transactions, the audit report should include administrative details designed to protect the transaction, such as encryption during transmission. For IT services like hosting and data storage, the report should detail how data integrity is maintained within these services.
- Confidentiality: The audit document should specify any restrictions on data sharing, storage, transfer, and access methods, as well as procedures to comply with privacy policies, such as employee procedures.
- Privacy: The organization’s privacy policy must be consistent with its actual operating procedures. For instance, if a company claims to warn customers every time it collects data, the audit document must accurately describe how warnings are provided. Personal data management must, at a minimum, follow the AICPA’s Privacy Management Framework (PMF).
SOC 3 Compliance
SOC 3 outlines information about a service organization’s internal controls for security, availability, processing integrity, confidentiality, and privacy. Based on AICPA Trust Services Criteria, SOC 3 reports are part of the voluntary SOC compliance reports, including SOC 1 and SOC 2 audits.
Typically requested by user entities or potential clients, SOC 3 audits are conducted by a certified public accountant or an accredited third-party auditor. Organizations that handle sensitive customer or personal data, such as software as a service, cloud computing, or data center storage providers, are more likely to undergo a compliance audit. Industries like finance, healthcare, e-commerce, and government also commonly use SOC 3 reports.
SOC 3 compliance is essential for the following reasons:
Brand reputation: SOC 3 reports assure clients that an organization’s controls and processes for protecting sensitive customer data are up to industry standards, showcasing a strong commitment to security and transparency.
Marketability: As they are made public, SOC 3 reports help businesses attract potential customers by demonstrating appropriate, secure controls for managing and protecting their data.
Risk management: SOC 3 standards enable organizations to assess their risk management processes and optimize their network management controls, reducing costs associated with security breaches.
Regulatory compliance: Similar to regulations like the EU’s General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA), SOC 3 compliance is another way of proving adherence to industry standards.
While SOC 2 and SOC 3 audits share similarities, there are differences between the two:
SOC 2 audits are restricted-use reports intended for management, stakeholders, and the client that requested the audit. They can be either Type I or Type II reports and may include confidential information.
SOC 3 audits are general-use reports intended for public use and distribution. They are always Type II and provide a high-level overview of a company’s controls, without disclosing confidential or detailed information.
SOC 3 compliance applies to any service provider, especially those handling sensitive customer data and aiming to prove compliance with strong industry standards. Cloud service providers, financial institutions, healthcare providers, retail and e-commerce businesses, and government agencies are among those most likely to seek SOC 3 compliance.
The SOC 3 audit process involves four steps:
Auditor: Hire an AICPA-certified CPA firm to conduct the audit.
Assessment: The auditor evaluates the service organization’s controls and risk management program based on the AICPA’s TSC standards, including on-site inspections, systems testing, employee interviews, and document reviews.
Attestation report: The auditor prepares a report summarizing the assessment results, providing a statement of assurance that the organization has met data confidentiality, access, and integrity standards.
Publication: The organization can post its SOC 3 audit report on its website or include it in marketing or advertising campaigns.
Beginner’s Guide to SOC Compliance
How Do I Become SOC-compliant?
Becoming SOC compliant requires undergoing an audit by a certified CPA. To prepare for this audit and ensure success, companies should follow these steps:- Determine the SOC certification type: First, decide which type of SOC certification best suits your organization’s needs: SOC 1, 2, or 3. Each certification has a specific focus, so understanding your organization’s requirements is essential.
- Choose the audit type: Decide whether you want to pursue a Type 1 or Type 2 audit. Type 1 audits assess the design of controls at a specific point in time, while Type 2 audits evaluate the operational effectiveness of controls over a specified period.
- Assess current security controls: Compare your organization’s existing security controls to the relevant SOC standards. This will help you identify gaps or areas needing improvement before the audit.
- Gather documentation: Ensure all company documentation related to internal controls, policies, and procedures is complete and up-to-date. This will smooth the audit process and help demonstrate your organization’s commitment to security and compliance.
- Conduct a formal security assessment: Engage an external entity to perform a comprehensive security assessment. This will help ensure that your organization meets the standards required for certification and provide valuable insights into areas for improvement.
- Implement recommendations: Based on the security assessment, implement any recommended changes to your organization’s controls, policies, and procedures. This may involve updating systems, enhancing security measures, or refining processes.
- Schedule the audit: Once your organization is prepared, schedule the audit with a certified CPA. The auditor will evaluate your organization’s controls and provide feedback on compliance with the relevant SOC standards.
- Address audit findings: After the audit, address any findings or issues identified by the auditor. Implement corrective actions as needed to ensure full compliance.
- Obtain the SOC report: Upon successfully completing the audit and implementing any necessary changes, the auditor will issue a SOC report. This report demonstrates your organization’s compliance with the relevant SOC standards and proves your commitment to security and data protection.
How Long Does it Take to Get SOC Compliance?
The duration required to obtain SOC compliance varies depending on various factors such as organizational size and the complexity of your environment. Generally, most organizations can expect a timeline of 6-12 months to achieve SOC compliance. The process begins with thoroughly assessing your organization’s current security posture, which entails identifying potential risks and vulnerabilities. This step is critical as it helps you understand the areas that require improvement and lays the foundation for a successful compliance journey. Following this, you will need to implement necessary controls, policies, and procedures to mitigate identified risks. Next, your organization must engage an independent third-party auditor to perform a SOC audit. This audit verifies that your security controls are adequately designed and operating effectively. The auditor will then provide a report detailing their findings, which you can use to demonstrate compliance to stakeholders. Keep in mind that the timeline for SOC compliance can vary depending on your organization’s preparedness. If you’re starting from scratch, it may take longer to establish the required security framework and controls. On the other hand, organizations with a solid security foundation may experience a shorter compliance journey.Conclusion
It’s important to know the differences between SOC 1, SOC 2, and SOC 3 when it comes to cybersecurity. SOC 1 is focused on financial controls, SOC 2 is focused on security controls, and SOC 3 is focused on security controls with a focus being on use for a general audience. There are also two types of each category, type 1 and type 2. Type 1 is a point in time assessment of the company’s controls while Type 2 is performed over a period of time.
At Oppos, we help you navigate the complexities of SOC compliance. We can provide experienced and knowledgeable experts who are dedicated to understanding your specific security requirements and helping you reach certification status. Contact us today for more information. With our help, you can be confident that you have the best security measures in place to protect your business and its data.
Don't wait – secure your data and boost customer confidence with Oppos' SOC attestations!
SOC FAQS
SOC stands for Systems and organization’s controls when you’re referring to the compliance standard. It can also stand for Security Operations Center when you’re talking about cybersecurity operations in a business.
SOC compliance reports are documents that provide assurance that a company has met the security requirements of its customers or other third parties. SOC compliance reports are prepared by independent auditors and are based on an evaluation of a company’s controls and procedures.
SOC (service organization control) audits are a type of external audit that assesses the internal controls of a service organization. SOC audits are conducted by independent auditors and typically include a review of the service organization’s financial statements, control procedures, and internal controls. The results of a SOC audit are reported in a SOC report.
Any third-party vendors that store, process or transmit company data must have security controls in place according to the certification that the company is applying for. It’s the applicant company’s responsible to ensure that all third party vendors handle their data with due diligence.
Audits and recertification must be done at least annually.




