Penetration testing, or pen testing, is a simulated cyberattack where ethical hackers try to gain access to systems and data to find security vulnerabilities that could be exploited by malicious hackers. Pen tests are usually performed by authorized ethical hackers who have permission from the system owner to conduct the test.
The goal of a pen test is to find the system’s vulnerabilities and help the system owner fix them before they can be exploited by real-world attackers. In this article, we will look in-depth at what penetration testing is and why it is important. We will also explore the different methods and techniques used in pen testing so that you can better understand how ethical hackers find and exploit security vulnerabilities.

What is Penetration Testing
Penetration testing, commonly known as pen testing, is a method of evaluating the security of critical systems by simulating cyberattacks. Its primary purpose is to identify security weaknesses, allowing security professionals to address vulnerabilities and strengthen security controls. There are several methods of pen testing employed by security professionals, including:- External testing: External pen testing focuses on assets visible on the internet, such as the web application, company website, email servers, and domain name servers (DNS). The main objective is to gain access to these assets and extract valuable data, assessing the vulnerability of an organization’s external-facing systems.
- Internal testing: Internal pen testing involves simulating an attack by a malicious insider with access to an application behind the firewall. This method does not necessarily simulate a rogue employee; it could also mimic a scenario where an employee’s credentials were stolen due to a phishing attack. Internal testing helps evaluate the potential damage an insider threat could cause.
- Blind testing: In blind pen testing, the tester is only provided with the name of the target enterprise. This approach offers security personnel a real-time perspective on how an actual cyberattack would unfold, enabling them to assess their detection and response capabilities.
- Double-blind testing: Double-blind testing involves security personnel having no prior knowledge of the simulated attack. This method tests the security team’s ability to react to an unexpected breach, closely mirroring real-world situations where defenses must be maintained without advanced warning.
- Targeted testing: Targeted pen testing is a collaborative effort between the testing team and the security personnel. They work together and inform each other of their actions, providing the security team with real-time feedback from the pen tester’s perspective. This method serves as a valuable training exercise to enhance the security team’s understanding of potential attack vectors and improve their defensive capabilities.
What are the Objectives of Penetration Testing?
The primary objectives of pen testing are to identify security weaknesses in computer systems, networks, and applications. It evaluates the effectiveness of security measures in place. By simulating real-world attacks, pen testing helps organizations to address potential security issues proactively and minimizes the risk of breaches. Some specific objectives of pen testing include:- Evaluating the effectiveness of security policies: Pen testing assesses the robustness of an organization’s security policy, identifying potential deficiencies that attackers could exploit. The insights gained from pen testing can help organizations revise their policies or improve employee training programs.
- Ensuring compliance with regulations and standards: Many industries are subject to regulatory requirements and standards, such as HIPAA and PCI. Pen testing helps organizations ensure they comply with these requirements, preventing potential fines and loss of business privileges.
- Assessing employee security awareness: Pen testing can evaluate employee responses to social engineering attacks, phishing attempts, and other security threats. By testing employee security awareness, organizations can identify areas where additional training is needed and assess the effectiveness of their current training programs.
- Evaluating incident response effectiveness: Since security incidents can occur even in well-protected environments, it is crucial to assess the effectiveness of IT and security personnel’s response to such incidents. Penetration tests can simulate real-world attacks, providing valuable insights into the organization’s incident response capabilities.
- Identifying and patching detected vulnerabilities: Pen testing helps organizations identify vulnerabilities in their computer systems, networks, and applications. Organizations can strengthen their security controls by addressing these vulnerabilities and reducing the risk of successful cyberattacks.
- Enhancing web application security: Pen testing is an essential aspect of web application security, as it helps organizations fine-tune their security measures, such as web application firewalls (WAF), to better protect against attacks.
- Performing gray box testing and function testing: Gray box testing is a method of pen testing that combines elements of black box and white box testing, while function testing assesses the functionality of an IT system. Both of these testing methods help organizations better understand their security posture and make necessary improvements.
Who Performs Pen Tests?
Pen tests are executed by highly skilled individuals known as penetration testers or ethical hackers. These professionals possess extensive knowledge of IT systems and cybersecurity, employing hacking techniques to assist organizations in uncover vulnerabilities within their network infrastructure. By leveraging various methodologies, tools, and approaches, penetration testers simulate cyberattacks to assess the efficacy of an organization’s security measures, determining the extent to which a hypothetical threat actor could breach their defenses. Pen testers are typically experienced developers or security experts with advanced credentials, including pen testing certifications. These qualifications enable them to proficiently navigate complex IT systems and utilize penetration testing tools with the same proficiency as malicious hackers. This expertise is essential for conducting comprehensive and accurate assessments of an organization’s security posture. To ensure the effectiveness of a pen test, it is crucial to engage pen testers who have little to no familiarity with the system they are examining. This approach minimizes the risk of overlooking vulnerabilities due to inherent biases or preconceived notions about the system’s security. For instance, a developer conducting a pen test on their own source code may unintentionally neglect certain weaknesses that an external tester would identify. Pen testing teams, or “testing tea,” often comprise professionals with diverse skill sets and backgrounds to assess an organization’s security holistically.What are the 3 Types of Pen Testing?
There are three types of penetration tests:Black-box assessment
A black-box assessment penetration test is an unbiased evaluation of a system, component, or product that does not involve any direct examination or testing of the internal workings of said system, component, or product. Black-box assessments are conducted from the outside, using only publicly available information. This type of assessment is often used to assess the security of a system, component, or product. It can also be used to assess the compliance of a system, component, or product with a set of security requirements or standards. Black-box assessments can be used to supplement other types of assessments, such as white-box assessments or gray-box assessments. When used in combination, these different types of assessments can provide a more complete picture of the security of a system, component, or product.White-box assessment
A white-box assessment penetration test is a type of security assessment where the tester has full knowledge of the system under test. This includes knowledge of the system’s design, implementation, and internal structure. White-box assessments are considered to be more thorough than black-box assessments, as they allow for a more in-depth analysis of the system. However, they also require more time and resources to conduct.Gray-box assessment
Gray-box assessment penetration test is a type of security assessment in which the assessor has some knowledge of the internal workings of the system under assessment. This type of assessment is contrasted with black-box and white-box assessments, in which the assessor has no knowledge or full knowledge, respectively, of the system under assessment. Gray-box assessments are useful in cases where the assessor needs to have some understanding of the system in order to effectively assess it, but cannot or does not want to have full knowledge of the system. This type of assessment can provide a more comprehensive picture of the system’s security than a black-box assessment, while still being less invasive than a white-box assessment.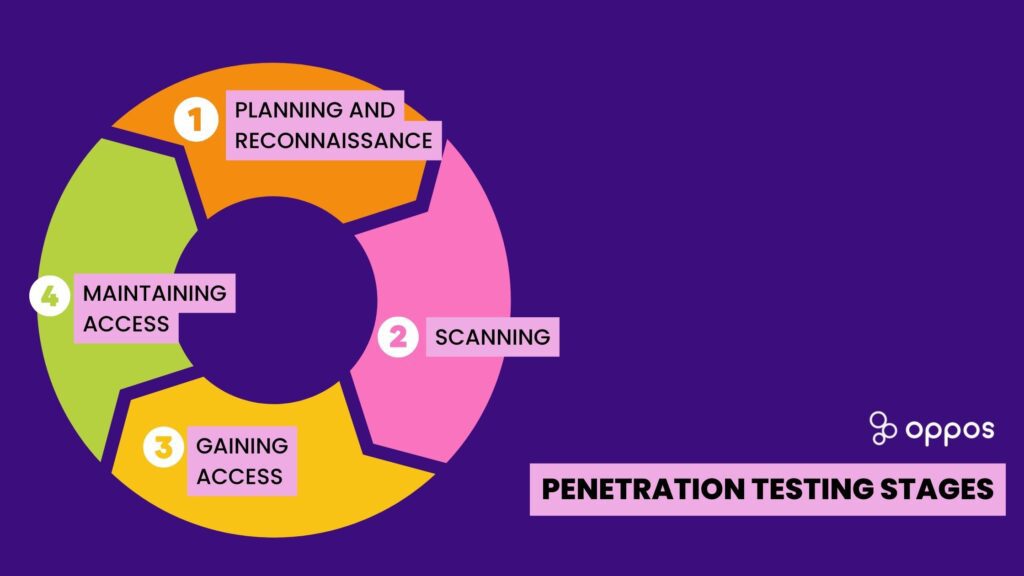
Penetration Testing Stages
Pen testers follow a structured process to perform penetration tests effectively and efficiently. The stages of penetration testing typically include:Planning and reconnaissance
Planning and reconnaissance are two of the most important steps in ethical hacking. Without proper planning and recon, an ethical hacker will not be able to find and exploit the vulnerabilities in a system. Planning involves figuring out the goals of the hack and the systems that need to be targeted. It also involves creating a timeline for the hack and making sure that all of the necessary tools and resources are in place. Reconnaissance is all about gathering information about the target system. This includes doing things like port scans, domain lookups, and banner grabbing. It’s important to note that reconnaissance can be done both passively and actively. Active reconnaissance involves actually interacting with the system, while passive reconnaissance simply involves observing the system from a distance.Scanning
Scanning is a vital part of ethical hacking, as it helps assess the security of a system and identify any potential vulnerabilities. There are a variety of different scanning techniques that can be used, and each has its own advantages and disadvantages. NMap is one of the most popular scanning tools available, and it can be used to scan for a variety of different things, including open ports, operating systems, and service versions. NMap can be run on both Linux and Windows systems. Another popular scanning tool is SuperScan, which is designed specifically for Windows systems. SuperScan can be used to scan for open ports, ping sweep a range of IP addresses, and perform reverse DNS lookups.Gaining Access
Gaining access is the act of obtaining unauthorized access to a computer system. This can be done through a variety of means, such as exploitation of vulnerabilities, social engineering, and physical attacks. Once an attacker has obtained access to a system, they can then attempt to escalate their privileges to gain even more control. This is the first step in the actual hacking process. By getting access to a system, an ethical hacker can then begin to assess the internal security of the system and look for ways to improve it. By doing this, they can help organizations better protect themselves against attacks.Maintaining Access
In ethical hacking, maintaining access is key to being able to continue your assessment and perform any necessary follow-up tasks. There are a few ways to maintain access, and the most common is to use a backdoor. A backdoor is a method of circumventing normal authentication procedures to gain unauthorized access to a system. Backdoors can be placed in systems by attackers during an initial breach, or they can be built into systems by malicious insiders. Once an attacker has a backdoor in place, they can use it to return to the system at any time, even if the original vulnerable entry point has been fixed.Who Needs Penetration Testing?
Cybersecurity is important for all businesses, but especially for companies that handle sensitive data or that are at high risk for cyberattacks. If your company falls into one of these categories, you should strongly consider investing in penetration testing services. Penetration testing is a form of security testing that simulates a real-world cyberattack. By hiring a professional penetration tester, you can ensure that your cybersecurity defenses are up to the task of repelling a real attack. This is an important step in protecting your business, and it can give you peace of mind knowing that you’re prepared for the worst. If you’re not sure whether your company needs penetration testing, ask yourself the following questions:- Does your company handle sensitive data?
- Are you at high risk for cyberattacks?
- Do you have a robust cybersecurity defense?
What Happens in the Aftermath of a Pen Test?
A penetration test, also known as a pen test, is a simulated cyber attack against your company’s system to check for vulnerabilities. After the test is complete, it’s important to debrief with your team and review the findings. This will help you understand what areas need improvement and how to better protect your system in the future. Here are a few things you should do in the aftermath of a pen test:- Review the findings with your team.
- Make changes to your system based on the findings.
- Test your system again to make sure the changes are effective.
- Keep your team updated on the changes you’ve made.
- Stay vigilant and continue to monitor your system for any new vulnerabilities.
Penetration Testing by Oppos
Penetration testing is a simulated attack on a computer system, network, or web application to find security vulnerabilities. It is a type of security testing that is used to find flaws in a system before attackers do. Penetration testing can be used to test the security of an organization’s IT infrastructure, networks, web applications, and more. It is a vital part of any security program.
Don’t leave your organization vulnerable to cyber threats! Opt for Oppos Cybersecurity Testing Services to identify, evaluate, and eliminate security weaknesses. Our team of certified ethical hackers conducts real-world attack simulations, exposing potential risks before malicious hackers exploit them. Strengthen your cyber defenses and gain peace of mind with our comprehensive, tailored solutions. Don’t wait for a breach to happen; act now and secure your digital assets.
Don't wait – secure your data and boost customer confidence with Oppos' penetration testing services.
Penetration Testing FAQS
A vulnerability assessment focuses on identifying and categorizing system vulnerabilities, while penetration testing attempts to exploit system vulnerabilities to determine if unauthorized access or other negative consequences could occur.
For a successful penetration test it’s important to have a clear plan/objective, an experienced team, good security tools and the support of upper management to remediate any findings.
It’s best to limit the scope of penetration testing to either meeting compliance requirements and/or improving the security of a specific part of the organization based on business requirements.
Penetration testing can present key challenges such as downtime risks, unclear objectives, insufficient testing environments, and vague vulnerability remediation instructions; however, thorough planning, clear communication with pen testers, and maintaining a dedicated testing environment can effectively mitigate these issues.
Penetration testing is used to ensure that organization’s have the proper security controls in place and working to meet their regulatory and industry standards.






