The Federal Risk and Authorization Management Program (FedRAMP) is a government-wide program that provides a standardized approach to assessing, monitoring, and authorizing cloud computing products and services. To ensure the security of sensitive data and information, FedRAMP mandates that all cloud service providers (CSPs) undergo regular penetration testing to identify and mitigate vulnerabilities. To facilitate this process, the FedRAMP Penetration Testing Guide was created to provide comprehensive guidance for CSPs seeking authorization. This guide outlines the scope, procedures, and requirements for conducting penetration testing in a FedRAMP-compliant manner.
In this blog, we will delve into the key aspects of this guide and provide valuable insights for CSPs seeking FedRAMP approval.

Does FedRAMP require a pen test?
The short answer is that FedRAMP requires a pen test as part of its security assessment process. Specifically, FedRAMP requires that cloud service providers (CSPs) undergo a vulnerability assessment, which includes a pen test, to identify security weaknesses and potential vulnerabilities in their cloud-based information systems. It’s important to note that the pen test is just one part of the overall security assessment process. CSPs must meet many other FedRAMP requirements, such as data backup and recovery, access control, and incident response, to achieve and maintain FedRAMP compliance. Overall, FedRAMP’s pen test requirement is just one of many necessary steps in ensuring secure cloud-based information systems for use by federal agencies and their clients.
During initial certification, the pen test must be performed by a fedRAMP 3PAO. This stands for Third Party Assessment Organization and they must be the ones to perform the initial security assessments as well as the annually required pen tests following certification.
What security assurance does FedRAMP provide?
There are many security concerns associated with cloud computing, especially when it pertains to sensitive government data. The Federal Risk and Authorization Management Program (FedRAMP) was created to help alleviate these concerns by providing a standardized approach to security assessments, authorization, and continuous monitoring for cloud service providers.
FedRAMP sets rigorous security standards that cloud service providers must meet in order to receive authorization to work with government agencies. This includes stringent requirements for access control, data protection, security monitoring, and incident response planning. Additionally, FedRAMP ensures that cloud service providers undergo regular security assessments and adhere to continuous monitoring requirements to maintain their authorization.
By providing assurance that cloud service providers meet strict security standards and undergo continuous monitoring, FedRAMP offers government agencies peace of mind when it comes to the security of their data. With the use of cloud computing on the rise in the public sector, FedRAMP plays an important role in strengthening the overall security posture of the federal government.
What is Penetration Testing: An In-Depth Guide to Ethical Hacking
FedRAMP compliance requirements
Ensuring compliance with the Federal Risk and Authorization Management Program (FedRAMP) is a critical requirement for any company providing cloud-based services to federal agencies. FedRAMP provides a standardized approach to security assessment, authorization, and continuous monitoring for cloud products and services. To meet FedRAMP compliance requirements, a company must undergo a rigorous security assessment and authorization process, which includes a detailed review of security controls, policies, and procedures. This process involves working closely with an accredited third-party assessment organization (3PAO) to ensure that all FedRAMP controls are properly documented and implemented.
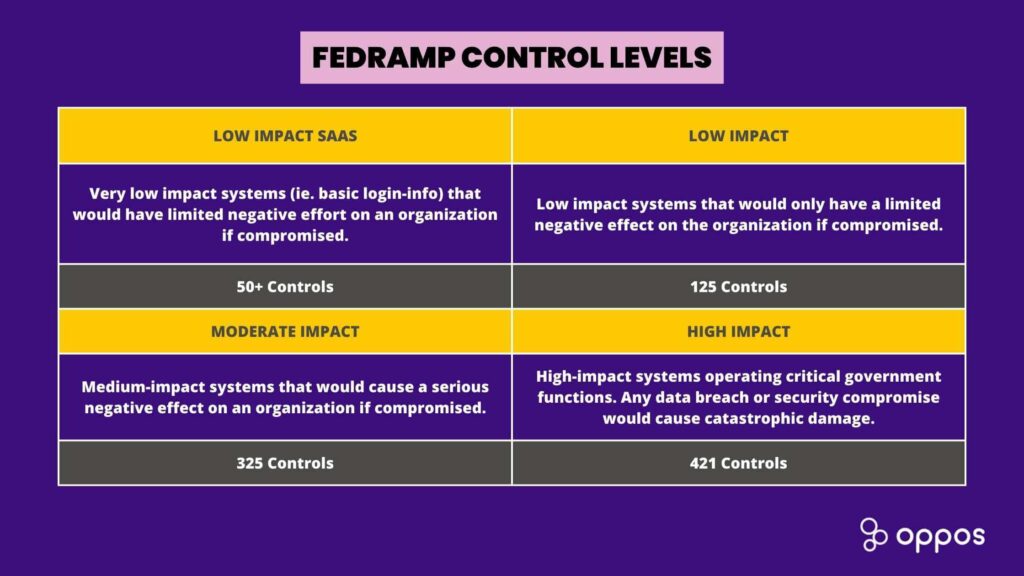
FedRAMP Compliance is based on four different impact levels:
FedRAMP Impact Levels
Federal Risk and Authorization Management Program (FedRAMP) Impact Levels are an essential aspect of the FedRAMP Authorization process. These Impact Levels are determined by assessing the potential impact to organizations and systems if confidentiality, integrity, or availability of their information were compromised. The Impact Levels are classified as Low, Moderate, or High, with each carrying specific security requirements that must be met.
Organizations looking to achieve FedRAMP authorization must understand the Impact Levels and ensure they meet the corresponding security requirements. The Impact Level chosen is dependent on the sensitivity and criticality of the data processed, stored, or transmitted by the system. This ensures that the system undergoes a rigorous security assessment and has appropriate controls in place to protect the confidentiality, integrity, and availability of information.
- High: For systems in this category “The loss of confidentiality, integrity, or availability could be expected to have a severe or catastrophic adverse effect on organizational operations, organizational assets, or individuals.
- Moderate: For systems in this category “The loss of confidentiality, integrity, or availability could be expected to have a serious adverse effect on organizational operations, organizational assets, or individuals.”
- Low: For systems in this category “The loss of confidentiality, integrity, or availability could be expected to have a limited adverse effect on organizational operations, organizational assets, or individuals.”
- Low-Impact Software-as-a-Service (LI-SaaS): For systems in this category “systems that are low risk for uses like collaboration tools, project management applications, and tools that help develop open-source code.”
Completion of FedRAMP documentation requirements
When it comes to obtaining FedRAMP certification for your cloud service offering, documentation is a critical component of the process. The Federal Risk and Authorization Management Program (FedRAMP) requires that cloud service providers (CSPs) provide a range of documentation to demonstrate compliance with the program’s rigorous security requirements.
The FedRAMP documentation requirements include a System Security Plan (SSP), a Security Assessment Plan (SAP), a Security Assessment Report (SAR) and a Plan of Actions and Milestones (POA&M). Each of these documents provides detailed insight into the security measures implemented by the cloud service provider to ensure the confidentiality, integrity, and availability of the data hosted in their cloud environment.
The SSP outlines the security controls implemented by the CSP, while the SAP details the approach to be taken in conducting a security assessment of the cloud service. The SAR provides details on the results of the security assessment, while the POA&M describes the steps the CSP will take to mitigate any identified security vulnerabilities.
To successfully achieve FedRAMP certification, CSPs must provide comprehensive and well-written documentation that demonstrates their adherence to FedRAMP requirements. This requires collaboration between technical and non-technical personnel to ensure that the documentation accurately reflects the security controls in place and the processes used to maintain and update them.
Implementing controls in line with FIPS 199 categorization
The Federal Information Processing Standard (FIPS) 199 categorization provides a framework for assessing the potential impact of a breach or compromise of a system’s confidentiality, integrity, and availability (CIA). As such, it is imperative for organizations to consider FIPS 199 categorization when implementing controls to ensure the security of their information systems as it relates to FedRAMP. Organizations must implement controls appropriate to the level of potential impact a system could have on their environment if compromised.
Third-party assessment (3PAO) of CSO
For this requirement, all organizations must have a third-party assessment performed on their organization to ensure compliance with fedRAMP standards. Additionally, you must be documented proof of the testing and that your organization passed the testing successfully.
Development of a Plan of Action and Milestones (POA&M)
A Plan of Action and Milestones (POA&M) is a collaborative management tool that outlines specific actions and targets for resolving vulnerabilities in information systems and networks. It is a crucial component of any organization’s cybersecurity strategy, and a key factor in maintaining compliance with regulatory requirements such as fedRAMP, FISMA and NIST 800-53.
The purpose of a POA&M is to identify and document all vulnerabilities that have been identified in the organization’s assets, and to set forth a plan to prioritize and remediate each vulnerability based on risk and criticality. The POA&M also establishes a timeline for the completion of each action item, sets forth responsible parties for each action, and identifies the resources required to complete the mitigation.
This document is essential for organizations to track progress and ensure that all identified vulnerabilities are addressed in a timely manner. It allows for organization-wide collaboration and transparency in the remediation process, ensuring that all stakeholders are aware of remediation progress and any potential roadblocks.
In summary, a POA&M is a structured and detailed plan that outlines the actions required to address identified vulnerabilities, sets priorities, and establishes timelines for remediation. It is a critical component of any comprehensive cybersecurity strategy and is essential in maintaining compliance with regulatory requirements.
Obtaining a provisional ATO (P-ATO) from the Joint Authorization Board (JAB) or agency-specific ATO
ATO stands for authorization to operate and it gives organization’s the right to operate their business legally. n the context of government agencies and contractors, this process is a critical component of information technology (IT) security compliance. Obtaining an ATO helps ensure that the system or network has been thoroughly tested and evaluated for risks and vulnerabilities before they are used for business purposes.
Implementing a Continuous Monitoring (ConMon) program, including monthly vulnerability scans
Implementing a Continuous Monitoring (ConMon) program, including monthly vulnerability scans, is critical for businesses to ensure the security and protection of their assets. A ConMon program involves ongoing monitoring of security controls and detection of potential threats or vulnerabilities. By conducting monthly vulnerability scans, businesses can detect any weaknesses in their systems and take action to address them before they can be exploited by malicious actors. This is part of an organization’s ongoing responsibility to security in their organization.
Mandatory FedRAMP Attack Vectors
Attack vectors are different potential entry points into an organization that may lead to loss or degradation of system integrity, availability or confidentiality. FedRAMP has identified several risk scenarios that should be reviewed or addressed during penetration testing.External to Corporate (External untrusted to Internal untrusted)
According to the FedRAMP testing guide ” The External to Corporate attack vector requires the execution of a social engineering (phishing) attack against a CSP’s system administrators, and managing personnel who may influence system administrators”. It requires a detailed phishing campaign be carried out with the end goal of seeing if they can trick someone into performing an action that would give potential attackers access to the systems.
Target System to CSP Management System (External trusted to Internal trusted)
For this attack vector “The External to CSP Target System attack vector simulates and tests vulnerabilities from external threat actors and untrusted Internet-based attacks; internal threats such as weak permissions/access controls and abuse of system services; and poor customer separation measures (e.g., improper network segmentation and poor implementation of security controls).”. This is the most common type of penetration testing activity as it seeks to evaluate common technical security controls for any potential weaknesses from an outsiders perspective.
Tenant to Tenant (External trusted to External trusted)
For this attack vector “the Tenant to CSP Management System attack vector simulates and tests vulnerabilities, untrusted internal threats, and trusted internal threats that emanate from network threat actors, application threat actors, and abuse of services of the authorized system. This attack vector is performed by conducting a full application test attempting to access CSP management systems due to misconfiguration, flaw in system design, abuse of intended function, low-code or no-code software deployment, and/or command line interface (CLI) that allows access to the CSP management zone. This type of testing will act similar to the above vector however the test is beginning from a typically customer user that has some access to the external application.
Corporate to CSP Management System (Internal untrusted to Internal trusted)
For this attack vector “This attack vector simulates and tests vulnerabilities from untrusted internal threats and trusted internal threats that emanate from issues such as ransomware spread from government and multi organization access to the authorized system.” This type of testing takes place on a privileged account within the corporate network, the accounts should have access to the highest level of access that a customer user could have.
Mobile Application (External untrusted to External trusted)
Last but not least this attack vector “consists of emulating a mobile application user attempting to access a CSP target system or CSP management system. This attack vector is tested on a representative mobile device and does not directly impact a CSP target system or infrastructure. Information derived from this activity can be used to inform testing of other attack vectors. If a mobile application is not part of a CSP’s CSO, then this attack vector can be marked as out-of-scope.” This vector is very straight forward but includes testing from the point of view of a mobile user.
FedRAMP requirements for Third-party Assessment Organization (3PAO)
To become a FedRAMP-authorized 3PAO, there are specific requirements that must be met. These include a thorough understanding of the FedRAMP process and requirements, as well as experience in conducting security assessments and audits. Additionally, 3PAOs must have a strong understanding of the cloud computing environment and the associated risks. Lastly the company must be accreditation by the American Association for Laboratory Accreditation (A2LA). There are few certifications that are highly respected in the industry that are a sign that the someone is a component tester of information systems: Offensive Security’s OSCP, OSCE, Global Information Assurance Certification’s GWAPT, GPEN, GXPN and EC-Council’s CEH and LPT.Conclusion
In conclusion, the FedRAMP Penetration Testing Guide serves as an essential resource for any organization seeking to achieve compliance with the Federal Risk and Authorization Management Program. This guide provides crucial insights into the testing process, including scope definition, vulnerability scanning, and reporting. We have condensed much of the important information into this blog post but that is no substitute for true professional guidance.
Oppos Cybersecurity Consultants specialize in helping organizations prepare for security assessments and audits. We have over +20 years of experience helping organizations of all sizes reach their compliance goals. To speak with one of our consultants reach out to us via our contact form and to stay informed on the latest developments in FedRAMP compliance and cybersecurity best practices, be sure to subscribe to our newsletter for more tips and guidance.
Don't wait – secure your data with Oppos' Penetration Testing
FedRAMP Penetration Testing FAQS
SOC is another security compliance standard/certification but it is general use for many industries while fedRAMP is focused on government/federal agencies.
FedRAMP provides assurance that the company meets the security standards outlined by the federal government, which includes strong assurances of confidentiality, integrity and availability of company systems.
FedRAMP is a federal standard so the standards are quite high compared to other general use security standards.
FedRAMP high compliance is an impact level that applies to security systems that would have a large impact on the company if it were to be compromised.






