
The zero-trust model is one of the core security concepts that emphasize the importance of authenticating all users before giving them access to company resources. The zero-trust model as the name suggests means that you shouldn’t implicitly trust anyone, regardless of where the request is coming from. This means inside the network, outside the network, or coming from a trusted network you should still have processes in place that require a user to authenticate before giving them access to a company resource. This way regardless of where an attack is coming from, they won’t be able to bypass the security mechanisms that you have in place. Here are some of the most important things you need to do to implement this properly:
1) Identify targets for cyberattacks
Not all resources on the network are equally valuable. You want to focus on assets that are likely to be targeted during a cyberattack and those are the resources that you want to require people to authenticate to access. Some examples of this are things like privileged accounts e.g. admin accounts, databases that hold customer information, documents that have important business plans, etc.
2) Utilize MFA
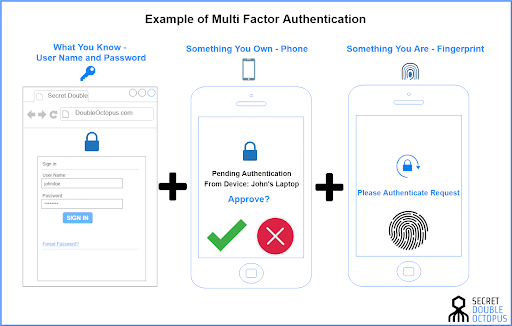
Multi-factor authentication is very important for a zero trust model, especially for resources that are being accessed from inside the network. You want to make sure that you implement MFA so that attackers can’t easily hijack accounts and use them to access multiple network resources. One way that companies like to implement this is using MFA combined with SSO so that employees don’t have the inconvenience of having to log in multiple times but still have the security provided through MFA.
3) Ensure you have the right security controls to enforce authentication
This includes many things but you need to make sure that authentication is properly enforced. There’s no point in having the features for someone to be authenticated if it’s easy for someone to circumvent the controls and get access to resources through other means.
4) Give just enough access
This goes back to the concept of least privilege, but you don’t want to give people access above what they need. Any additional access above what is needed could be used to perform malicious actions on the network and it represents risk without any possible reward, so be sure to limit access to only what is needed.
5) Use PAM tools where appropriate
This stands for privileged access management and this means having controls to protect accounts that present an above-average amount of risk. Using PAM tools can provide the following controls for both applications and infrastructure “1) Storage of credentials in a centralized, enterprise-grade vault; 2) strong authentication for retrieval of credentials by authorized users; 3) automatic rotation of credentials; 4) revocation of access in the case of anomalous behavior, and 5) time-of-day restrictions.” According to techrepublic.com.
How to get more free content
If you like this article and would like to read more of our content for cybersecurity insights, tips and tricks feel free to follow us on our social media. If you’re a struggling business owner who needs help in assessing their business’s cybersecurity posture feel free to take advantage of our free introductory assessment and we’ll help you figure out a game plan for keeping your company safe.





