Canadian businesses face an ever-evolving landscape of cybersecurity threats and regulatory demands in the digital age. Oppos’ SOC 2 Compliance Attestation Service is designed to help businesses navigate this complex terrain. Our comprehensive solution secures sensitive data and strengthens trust with clients. Our service is tailored to meet the rigorous standards of SOC 2, focusing on the five trust services criteria: security, availability, processing integrity, confidentiality, and privacy.
At Oppos Cybersecurity Compliance, we understand the paramount importance of protecting customer data. Our cybersecurity specialists follow a thorough approach to assess and improve your internal controls and information security practices. We strictly adhere to the SOC 2 compliance framework to assist service organizations in Canada in strengthening their data security measures. We aim to safeguard personally identifiable information and sensitive data against any potential breaches.
We specialize in simplifying the complex SOC 2 certification process to make it a seamless journey for our clients. Our thorough assessments evaluate the design and effectiveness of your service organization’s controls while providing useful insights to enhance your overall security posture. We offer guidance on specific business practices and risk management strategies that align with the relevant trust principles, giving you the best chance to achieve successful SOC 2 attestation.
Partnering with Oppos for SOC 2 attestation is not just about achieving compliance. It demonstrates your commitment to data integrity and client trust, which is a competitive advantage in today’s market. SOC 2 certification reflects your organization’s dedication to upholding the highest data security and processing integrity standards.
With Oppos as your trusted partner, you can be confident in your ability to prioritize and effectively manage your clients’ data’s security, confidentiality, and privacy.

What are SOC 2 Audit Compliance Standards?
SOC 2 (Service Organization Control 2) audit compliance standards were developed by the American Institute of Certified Public Accountants (AICPA). These guidelines help service organizations demonstrate their commitment to managing and securing customer data based on five Trust Services Criteria (TSC): Security, Availability, Processing Integrity, Confidentiality, and Privacy.
SOC 2 standards are particularly relevant to technology and cloud services companies that handle customer data. They ensure that these companies maintain high information security and process integrity.
Key Components of SOC 2 Compliance Standards
- Security: The security principle aims to protect system resources from unauthorized access. Access controls prevent potential system abuse, theft, data removal, software misuse, and information alteration or disclosure.
- Availability: The availability principle concerns ensuring that the system, products, or services are accessible as per the terms of the contract or service level agreement (SLA). Although it does not guarantee perfect uptime, the organization must take reasonable measures to ensure operational performance as agreed upon.
- Processing Integrity: This principle ensures that system processing is complete, valid, accurate, timely, and authorized to meet the organization’s objectives. It doesn’t imply perfection but demands that errors or defects are detected and corrected promptly.
- Confidentiality: Data designated as confidential, such as business plans, intellectual property, and internal company communications, is protected according to the organization’s commitments and agreements, focusing on preventing unauthorized disclosure.
- Privacy: The privacy principle encompasses the collection, use, retention, disclosure, and disposal of personal information by the organization’s privacy notice and the Generally Accepted Privacy Principles (GAPP).
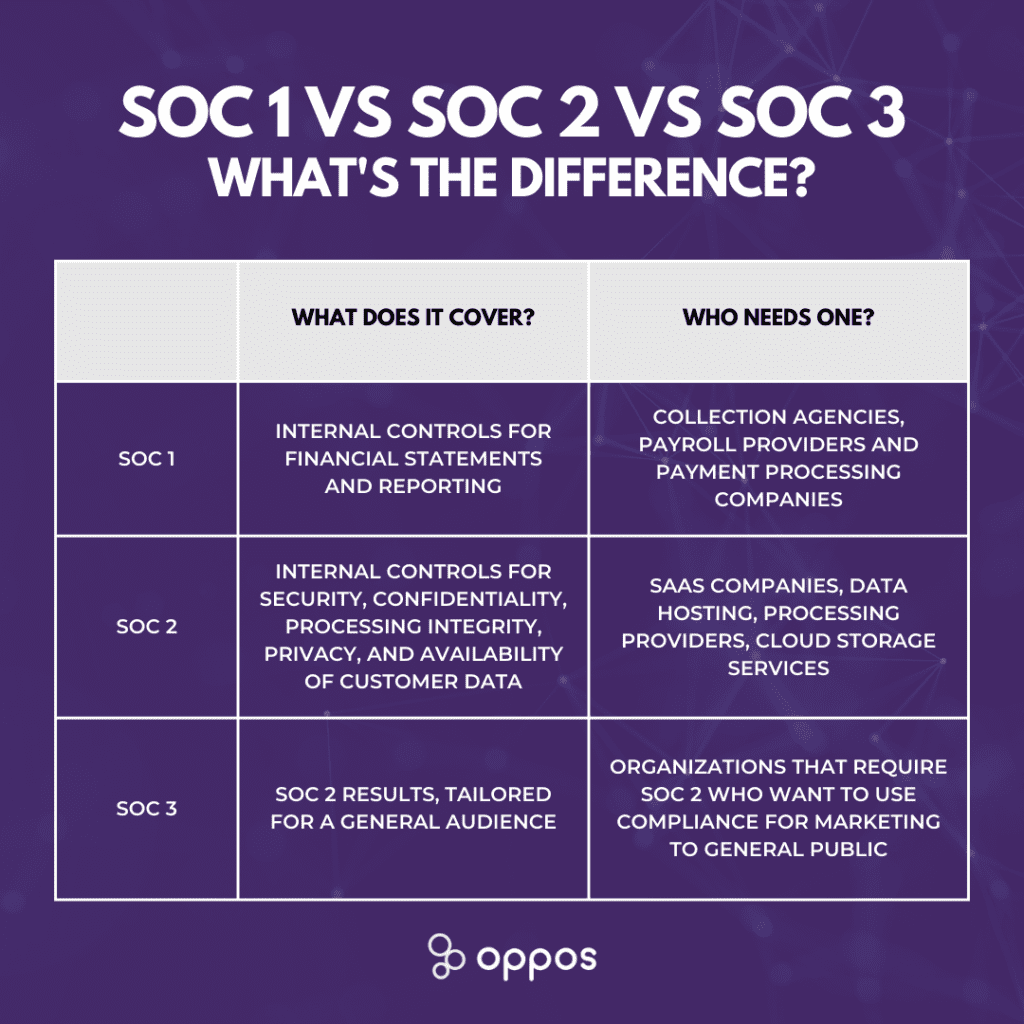
Why is SOC 2 Compliance Important?
In today’s digital age, data breaches are not just empty threats but real possibilities. This presents a critical challenge for Canadian businesses, as they must secure sensitive information and maintain client trust. SOC 2 Compliance is a reliable solution that goes beyond mere compliance by fostering a culture of security and integrity.
At Oppos SOC Compliance, we understand the unique landscape that Canadian businesses face, highlighting the need for a robust cybersecurity compliance framework that protects and enhances business value.
Why SOC 2 Compliance is Essential for Your Business
- Builds Trust with Clients and Partners: To gain the trust and loyalty of your clients and partners, it’s crucial to assure them that their sensitive information is handled with the utmost security and confidentiality. SOC 2 Compliance is the standard that demonstrates your commitment to data security and privacy in a world where data is as valuable as currency.
- Enhances Competitive Advantage: SOC 2 Compliance sets you apart from competitors in a crowded market. It shows your commitment to maintaining a secure and reliable environment, making your services more attractive to clients and stakeholders.
- Mitigates Risks of Data Breaches: With comprehensive controls and practices, SOC 2 Compliance helps identify vulnerabilities and mitigate risks associated with data breaches. This proactive approach safeguards your client’s data and protects your organization from the financial and reputational damage associated with security incidents.
- Streamlines Regulatory Compliance: SOC 2 Compliance helps Canadian businesses in regulated industries or handling sensitive data meet regulatory requirements by providing a structured framework to address the security, availability, processing integrity, confidentiality, and privacy of customer data, aligning with national and international standards.
- Fosters a Culture of Security: SOC 2 Compliance goes beyond a requirements checklist. It involves creating a security culture across the organization that safeguards information assets. It should be integral to your business operations, from top management to every employee.
Oppos Cybersecurity Compliance specializes in guiding North American businesses through SOC 1 Compliance and SOC 2. Our team of experts offers tailored solutions that fit your business needs, from initial assessment to ongoing compliance management. Trust us to ensure a smooth, efficient, and effective journey to SOC 2 Compliance.
Who Needs a SOC 2 Audit?
Technology and Cloud Services
SaaS companies, cloud hosting providers, and other technology service firms that manage customer data on their platforms.
IT Managed Services
Companies providing IT support, network services, and data management solutions.
Financial Services
Organizations handling financial transactions, payments processing, or financial data storage, where data integrity and confidentiality are paramount.
Healthcare Providers
If your organization offers data storage or management services, a SOC 1 audit ensures that your client’s financial information is handled securely and controlled.
Legal and Professional Services
Firms that manage sensitive client information and require stringent data protection measures.
E-commerce Platforms
Businesses that process customer transactions and store personal and payment information.
When Do You Need a SOC 2 Audit?
A SOC 2 compliance audit is not a one-time event; instead, it is an ongoing process of assurance that requires regular reassessment to ensure continuous compliance with the Trust Services Criteria. Typically, SOC 2 audits are conducted annually to provide service organizations with a current and valid attestation of their controls related to security, availability, processing integrity, confidentiality, and privacy.
Conducting annual SOC 2 audits ensures that the organization maintains continuous compliance with the relevant SOC 2 criteria, any changes to the organization’s services, controls, or processes are assessed and validated, and the organization can demonstrate to clients, partners, and stakeholders its ongoing commitment to protecting the security and privacy of user data.
Moreover, an organization may undergo additional SOC 2 compliance assessments under certain circumstances, such as significant changes in the internal control environment, IT infrastructure, or processes that could impact the handling and security of customer data, the introduction of new services or technologies that fall under the purview of SOC 2 compliance, mergers, acquisitions, or other organizational changes that could affect the previously assessed control environment.
Types of SOC 2 Reports
There are two types of SOC 2 reports: Type I and Type II. Each serves a distinct purpose and demonstrates different aspects of a service organization’s commitment to data security and control effectiveness.
Type 1 Report
The SOC 2 Type I report assesses a service organization’s system controls and suitability at a specific time. The report focuses on whether the controls are properly designed to meet the Trust Services Criteria for security, availability, processing integrity, confidentiality, and privacy. It assures clients and stakeholders that the organization has implemented security controls to protect customer data and ensure processing integrity.
Type 2 Report
SOC 2 Type II report assesses the operating effectiveness of the service organization’s controls over a specified period, typically at least six months. It demonstrates that the controls are appropriately designed and operating effectively.
Type II report is the more rigorous and informative of the two, offering a deeper insight into the organization’s security posture and operational effectiveness. It includes Evaluation of the effectiveness of the service organization’s controls over a period of time, detailed testing of the organization’s controls by certified public accountants or external auditors, and assurance to clients, business partners, and other stakeholders that the organization not only has proper controls in place but also maintains them effectively over time.
Ensure SOC 2 Compliance with Oppos
Why Choose Oppos for SOC 2 Attestation?
Oppos’ approach to SOC 2 compliance caters to North American regulations, offering a competitive advantage in both local and international markets.
Our team of experts specializes in the five trust services criteria – security, availability, processing integrity, confidentiality, and privacy. We ensure that your service organization’s system is designed with these criteria in mind. This helps protect customer data and ensure your service delivery’s integrity.
At Oppos, we comprehensively understand risk management and relevant trust principles. We assist you in recognizing and reducing risks related to handling sensitive data, such as personally identifiable information and intellectual property. We aim to ensure that your internal controls are strong and efficient.
Our methodology examines both the design and operating effectiveness of your service organization’s controls to ensure compliance and reliability of security and data protection measures.
We understand the importance of processing integrity in maintaining the accuracy and completeness of your client data. Our SOC 2 compliance services ensure that your systems operate effectively to safeguard the integrity of data processing, giving your clients unwavering confidence in your services.
In the event of security breaches or incidents, Oppos provides a proactive and strategic response plan. Our goal is to address immediate concerns and strengthen your security posture against future threats.
What to Expect for your SOC 2 Attestation Engagements
Partnering with Oppos for SOC 2 attestation is a strategic move for Canadian businesses to improve their data security, processing integrity, and customer data protection. It’s not just a certification; but a commitment to upholding the highest compliance standards. Here’s what businesses can expect when working with Oppos for their SOC 2 attestation journey:
Comprehensive Assessment and Planning
Oppos thoroughly assess your organization’s current security posture, focusing on the five trust services criteria. This sets up the SOC 2 engagement to address your business practices and risk management strategies. Based on your service organization’s system specifics, internal controls, and operating effectiveness requirements, we create a personalized SOC 2 compliance roadmap.
In-depth Understanding and Implementation
Our team of cybersecurity experts help your company personnel understand the nuances of the SOC 2 framework, including protecting customer data, internal reports, and maintaining a robust security posture against data breaches and security incidents. Oppos guides service organizations in integrating SOC 2 compliance standards into their daily operations, ensuring that controls meet the rigorous requirements set by the AICPA.
Rigorous Testing and Documentation
Oppos helps organizations prepare for SOC 2 audits by documenting controls related to data integrity, information security, and personally identifiable information. We conduct mock audits and rigorous control testing to identify and address potential issues, minimizing surprises during external auditor evaluations.
Ongoing Support and Continuous Improvement
Oppos assists with SOC 2 audits, liaising between your organization and the external auditor. We offer post-audit support, guiding on maintaining and improving your security controls and compliance posture, preparing for follow-up audits, and using SOC 2 compliance as a competitive advantage.
“A large Telco client of ours required Moveable Online undergo a PCI-DSS gap assessment. After asking around within our circle or business associates, we were introduced to Oppos. They were able to aid us with the gap assessment, make recommendations to secure our environment and help prepare the documentation our client required. The process was quick, informative and we will engage Oppos for future compliance related activities, primarily our efforts with achieving PCI-DSS compliance.”
“They weaved in a layer of security that we had only dreamed of in the past – a next generation rewall — which they built, congured and deployed at the perimeter of our network. When called upon, even with the great distance between us, they provide onsite or remote support as required and always meet the mark. Since the time of our initial project, we have called upon Oppos several times for various IT and Security related projects which they have delivered on every time.”
Partner with Oppos to Achieve SOC 2 Audit Compliance with Confidence
SOC 2 COMPLIANCE FAQS
SOC 2 compliance means an organization has met the rigorous standards of the American Institute of Certified Public Accountants (AICPA) for managing customer data based on five trust services criteria: security, availability, processing integrity, confidentiality, and privacy. It demonstrates a service organization’s commitment to safeguarding data and operating with high integrity and security practices.
Maintaining SOC 2 compliance involves regularly monitoring and updating internal controls to ensure adherence to the established criteria. This includes conducting periodic internal audits, addressing any deficiencies promptly, training employees on compliance requirements, and undergoing annual SOC 2 audits by a certified public accountant (CPA) to validate the effectiveness of security and privacy controls.
A SOC 2 report can only be provided by an independent CPA or a firm of certified public accountants accredited by the American Institute of Certified Public Accountants (AICPA). These auditors have the qualifications and expertise to conduct SOC 2 audits and assess an organization’s adherence to the relevant trust services criteria.
Implementing SOC 2 involves developing and enforcing policies and procedures that align with the AICPA’s trust services criteria. This process typically includes identifying relevant risks, designing and implementing controls to mitigate those risks, training staff on compliance requirements, and engaging a qualified CPA to conduct a SOC 2 audit to verify the effectiveness of these controls.
Assessing a SOC 2 report involves reviewing the auditor’s findings related to an organization’s controls over security, availability, processing integrity, confidentiality, and privacy. Key evaluation aspects include describing the service organization’s system, the auditor’s opinion on controls’ design and operating effectiveness, and any identified deficiencies or exceptions. This assessment helps stakeholders understand the organization’s commitment to safeguarding data.



